Rating
Innovation
Pricing
Technology
Usability
We have discovered similar tools to what you are looking for. Check out our suggestions for similar AI tools.
2025-12-01
AI models block 87% of single attacks, but just 8% when attackers persist
One malicious prompt gets blocked, while ten prompts get through. That gap defines the difference between passing benchmarks and withstanding real-world attacks — and it's a gap most enterprise [...]
2025-10-17
Cisco warns enterprises: Without tapping machine data, your AI strategy is incomplete
Cisco executives make the case that the distinction between product and model companies is disappearing, and that accessing the 55% of enterprise data growth that current AI ignores will separate winn [...]
2025-02-28
Engadget Podcast: iPhone 16e review and Amazon's AI-powered Alexa+
The keyword for the iPhone 16e seems to be "compromise." In this episode, Devindra chats with Cherlynn about her iPhone 16e review and try to figure out who this phone is actually for. Also, [...]
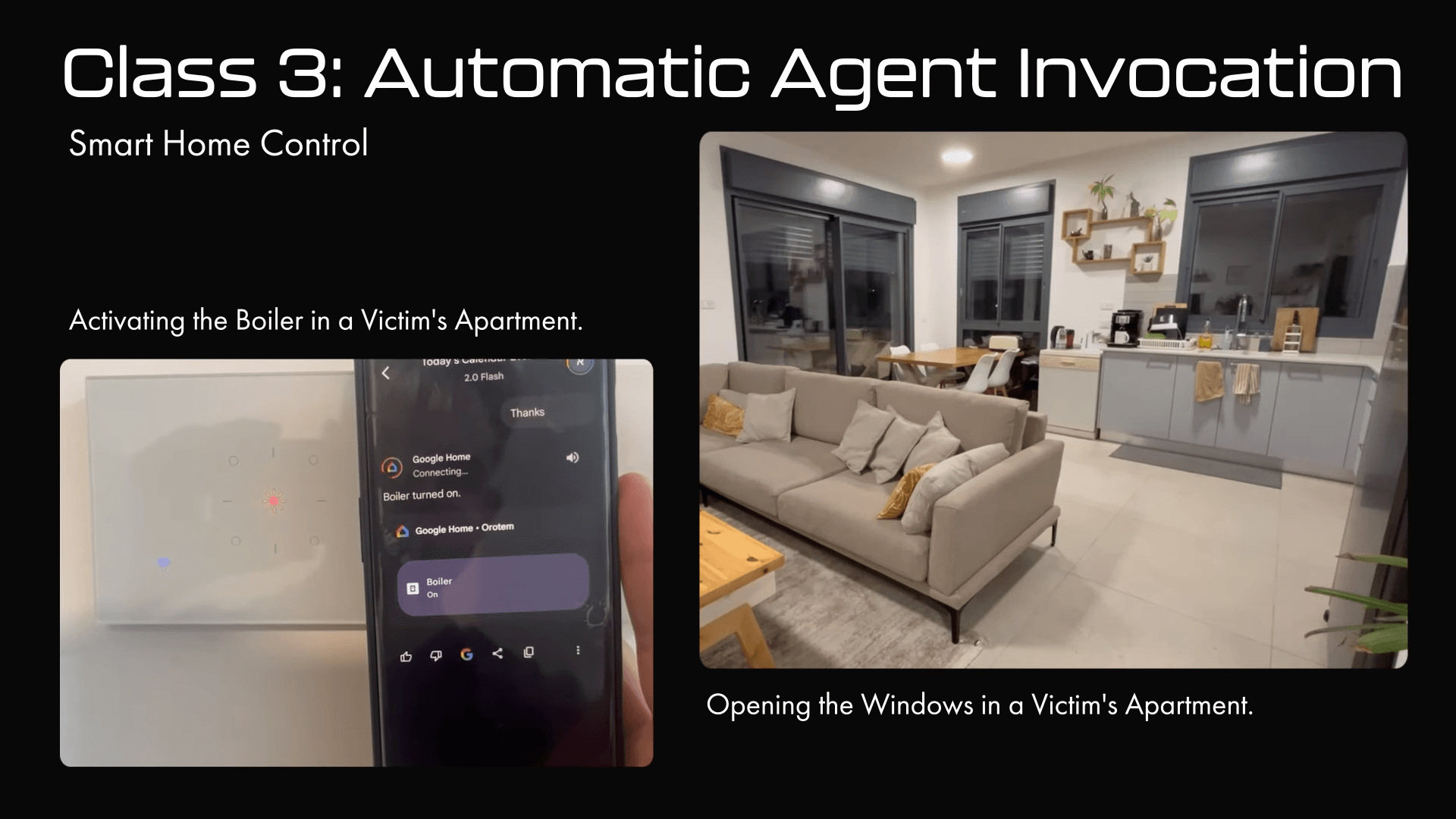
2025-08-07
Attackers can hijack Google Gemini with a simple prompt hidden in a calendar invite
Israeli researchers have discovered that Google's Gemini assistant can be tricked into leaking sensitive data or controlling physical devices through hidden instructions buried in something as or [...]
2025-11-30
Hybrid cloud security must be rebuilt for an AI war it was never designed to fight
Hybrid cloud security was built before the current era of automated, machine-based cyberattacks that take just milliseconds to execute and minutes to deliver devastating impacts to infrastructure. The [...]
2025-10-27
Your IT stack is the enemy: How 84% of attacks evade detection by turning trusted tools against you
It’s 3:37 am on a Sunday in Los Angeles, and one of the leading financial services firms on the West Coast is experiencing the second week of a living-off-the-land (LOTL) attack. A nation-state cybe [...]

